Dark web isn’t the usual internet that you access daily, in this article I will explore the hidden secrets of internet especially the Dark web and how you can access in in 2025.Inter is divided into three parts to surface web, Deep web and Dark web. Now you know, lets dive in
Dark web are internet resources that are hidden and it requires a special dark web browser to access it. These applications encrypts and routes traffic through several server layers around the world to hide your IP and provide you with private browsing.
Without any signal, all Dark webs are hidden in mystery and often carries a gloomy label like the black web or the underground internet. These names make it seem scarier than it really is. While it runs beyond the reach of standard search engines, it is not just a place for illegal things as you may think but it also allows people to stay anonymous, protect their privacy, and access information freely.
What is the difference in Dark web and deep web
Deep web are web pages that are not indexed by search engines like payment portals or login pages while the dark web operates on darknets that are only accessible using the special software. A lot of what you use online, like your email, bank account, private social media, and paid services, is part of the deep web. You wouldn’t want your emails to be public and easy for anyone to find. Typical browsers can’t access the dark web since it sits on darknets and its also part of the deep web.
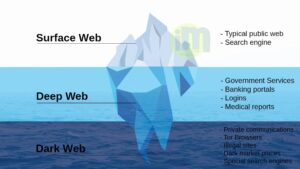
What activities runs on the Dark web market places?
While the dark web is used for illegal purposes, the dark web itself is not illegal either. its possible for one to buy or sell illegal stuffs like weapons, Malwares, drugs, credit cards and other prohibited contents. However, People can pay others to commit cybercrimes on the dark web.
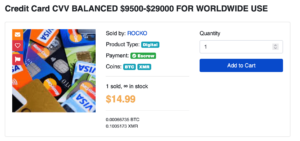
Here are some types of cybercrimes people can buy on the dark web
- Phishing email trics
- Ransomware Cyberattacks
- Email or social engineering
- Cyber espionage
- Malware development and distribution
- Botnet management
- Computer or network hacking
- Keylogger installation
- Refund scams
- Sensitive information exfiltration





